Introduction: Protect Yourself from DeFi Scams
The Problem
Decentralized Finance (DeFi) has revolutionized how we manage and grow our assets, offering unparalleled freedom and control. But with this freedom comes a dark side—DeFi scams. From phishing attacks to complex wallet exploits, scammers are constantly evolving their tactics to exploit the fast-paced and often unregulated nature of DeFi. If you're not careful, a single misstep could lead to catastrophic losses of your hard-earned funds.
Every day, unsuspecting users fall victim to DeFi scams, losing millions of dollars to malicious actors. What makes these scams even more dangerous is their complexity. A fake website or phishing email may seem easy to avoid, but what about sophisticated wallet scams or smart contract vulnerabilities? For newcomers and even seasoned investors, the learning curve can feel overwhelming. The rapid pace of technological evolution in DeFi has made staying safe a daunting challenge. Are you truly prepared to navigate this minefield?
The good news is that you don’t have to navigate the world of DeFi alone. This guide is designed to arm you with the knowledge and tools to recognize, avoid, and counteract DeFi scams—from the simplest phishing attempts to the most advanced wallet exploits. Whether you’re a crypto novice, an active DeFi investor, or someone exploring decentralized finance for the first time, this guide will empower you to safeguard your assets and confidently participate in the DeFi ecosystem.
What You'll Learn
In this comprehensive guide, you'll discover how to protect yourself from both basic and sophisticated DeFi scams. You'll learn:
- How to identify and avoid common scams like phishing and fake websites
- Ways to protect against complex threats such as malicious smart contracts
- Essential security practices for safeguarding your crypto assets
- Advanced protection strategies using hardware wallets and security tools
Are you ready to dive in and fortify your defenses against DeFi scams? Let’s get started!
Part 1: Easier-to-Avoid Scams
Let's start with the most common scams in DeFi that are relatively straightforward to identify and avoid once you know what to look for. While these scams might seem obvious to experienced users, they continue to be effective because they prey on human psychology and often target newcomers to the space. Understanding these basic scams will build a foundation for recognizing more sophisticated attacks.
Here are the five most prevalent types of basic DeFi scams:
1. Phishing Emails and Links
Phishing Emails in DeFi and Crypto
Although phishing scams are more common in the world of centralized exchanges (CEXs), they have found their way into DeFi as well. If you’ve ever registered on a CEX or provided your email to a crypto-related platform, chances are you’ve encountered phishing emails.
These emails typically mimic official communications from well-known platforms, using domains that closely resemble legitimate ones (e.g., lido.com instead of the actual lido.fi). The goal of these emails is to deceive you into taking actions that compromise your security, such as:
- Clicking links to fake websites.
- Entering sensitive information like private keys or seed phrases.
- Registering or logging in to fake platforms.
How Phishing Emails Work
Phishing emails operate by leveraging two key tactics:
1. Deceptive Domains:
The sender’s email domain often looks like the real one but includes subtle differences, such as @ledgernotice.com instead of the official @ledger.com. For instance:
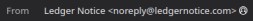
Here, the email mimics Trezor but uses a deceptive domain like @trezordilef.com.

2. Emotional Triggers:
These emails often use urgency or curiosity to prompt immediate action.
Claims like “Your account has been compromised!” or “Claim your exclusive NFT now!” are designed to make you act without thinking.
3. Malicious Links:
Links within these emails redirect you to fake websites that collect your information or trick you into approving malicious smart contract interactions.
Practical Prevention Tips
1. Double-Check Sender Domains
Inspect the email address carefully for subtle differences. For example:
- Fake:
support@ledgernotice.com - Real:
support@ledger.com
A fake email from MetaMask:
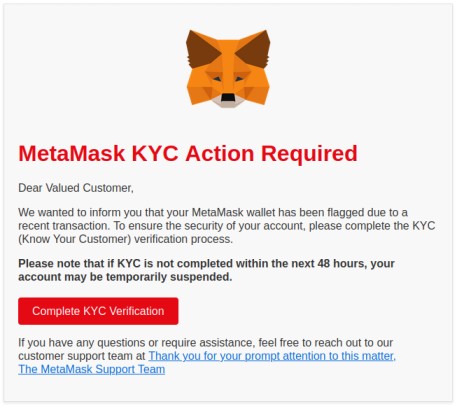
2. Never Click Links in Emails
Avoid clicking links in unsolicited emails, even if they seem urgent or exciting.
Instead, navigate to the official website directly by typing the URL in your browser.
3. Verify Suspicious Emails
If you’re unsure about an email, log in to the official website or contact the platform through verified channels.
A fake email from Lido:
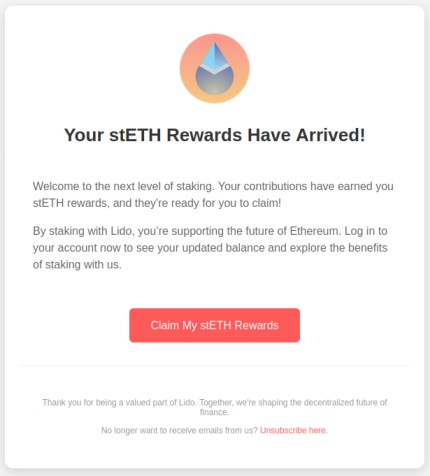
Key Takeaway
Phishing scams thrive on creating a false sense of urgency or opportunity. By staying vigilant, inspecting sender domains, and avoiding interaction with unsolicited emails, you can significantly reduce the risk of falling victim to these scams.
2. Social Media Impersonation
What Are Social Media Impersonation Scams?
Impersonation scams have become a significant problem across social media platforms, especially on platforms like Twitter (now X), where crypto discussions thrive. These scams involve fake profiles mimicking well-known influencers, projects, or companies to deceive unsuspecting users.
Fake accounts use sophisticated tactics, often copying everything from the real account’s bio, profile picture, and even tweets to create an illusion of legitimacy. They aim to gain trust and then exploit it.
Examples include:
A fake account of an influencer like “Charlie Lee” offering “LTC rewards.”
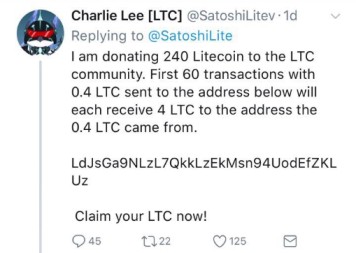
The account looks legitimate but is designed to steal funds by asking users to send crypto first to “claim rewards.”
An imposter pretending to be a project support agent, offering help but requesting wallet credentials or seed phrases.
How Do They Work?
Social media impersonation scams typically follow these steps:
1. Creating Fake Profiles:
Scammers create lookalike accounts, often adding subtle changes to usernames (e.g., @SatoshiLitev instead of @SatoshiLite).
2. Building Credibility:
These accounts interact with real users and mimic legitimate posts to appear authentic.
Some scammers even buy fake followers to bolster their credibility.
3. Scamming the Victim:
They promise free tokens in exchange for a small payment or wallet connection.
They pose as support representatives and request sensitive information to “help resolve an issue.”
Practical Prevention Tips
1. Verify Accounts Using Official Links
Always follow verified accounts through links on official websites or project announcements.
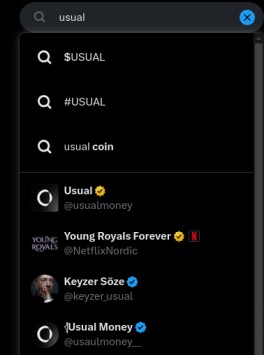
Check for subtle differences in usernames or profile handles. For example:
- Real:
@usualmoney - Fake:
@usaulmoney_
2. Avoid Direct Messages Offering Assistance or Investments
Be cautious of unsolicited DMs, even if the sender appears to be a trusted influencer or project.
Legitimate projects rarely ask for private keys, wallet credentials, or payments via DMs.
3. Report Fake Accounts
Most platforms have reporting features—use them to flag and report fake accounts.
This helps protect both you and the broader community.
Key Takeaway
Stay vigilant on social media, especially when interacting with crypto-related accounts. Verifying profiles and avoiding unsolicited requests are critical steps to staying safe from impersonation scams.
3. Website Spoofs
What Are Website Spoofs?
Website spoofs are fraudulent websites designed to mimic legitimate DeFi platforms, tricking users into connecting their wallets or entering sensitive information. These fake sites closely resemble the real ones, copying everything from layouts and logos to domain names, making them difficult to spot.
For example:
Searching for “Rabby Wallet” or “Rainbow Wallet” on Google may lead you to phishing websites near the top of the results, as shown below.
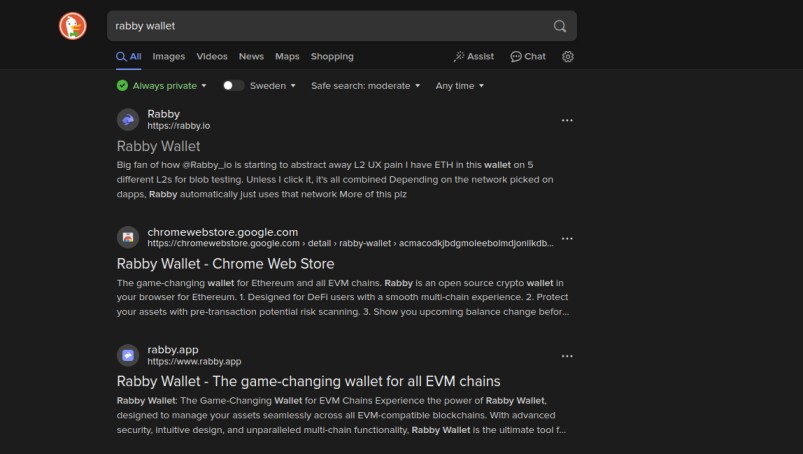
These sites often have slightly altered domain names (e.g., rainbow.cc instead of rainbow.me).
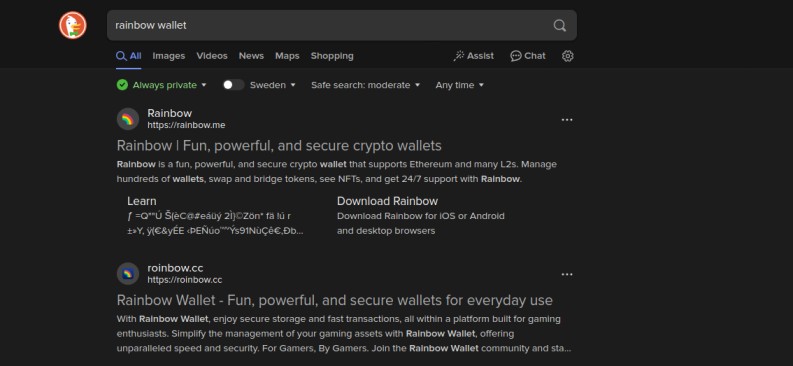
Once users access these sites, they are prompted to connect wallets or sign transactions, unknowingly granting scammers control over their funds.
How Do They Work?
Spoofed websites employ the following tactics to exploit users:
1. Deceptive Domains:
Scammers register domain names similar to legitimate ones, such as substituting letters (o with 0) or changing domain extensions (.io instead of .org).
2. Search Engine Manipulation:
These phishing websites may appear as top search results, either organically or through paid ads, targeting users looking for specific DeFi platforms.
3. Malicious Wallet Prompts:
Fake sites request wallet connections or approvals, leading to unauthorized access and theft.
4. Stealing Funds:
Once connected, scammers execute transactions to drain funds or approve malicious contracts.
Practical Prevention Tips
1. Verify URLs Before Visiting
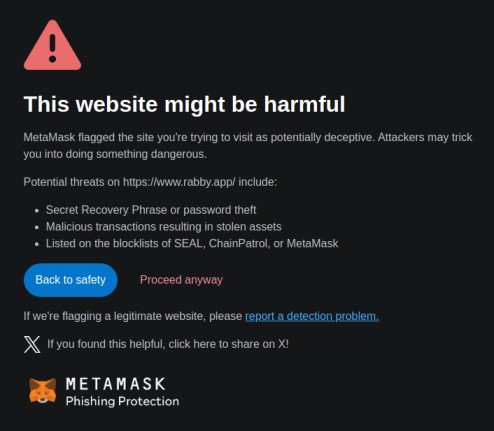
Double-check the website’s URL for subtle differences. Legitimate platforms often use secure HTTPS connections and their official domain names.
MetaMask’s phishing detection system flagged a fake Rabby Wallet URL:
2. Use Verified Sources
Start your research on trusted platforms like CoinGecko or CoinMarketCap, which provide links to official websites.
Cross-reference the links with project announcements on social media, such as Twitter.
3. Bookmark Official Websites
Create a personal bookmark folder for trusted DeFi platforms, wallets, and tools.
Once verified, use bookmarks instead of searching for the website repeatedly.
Key Takeaway
Website spoofing scams rely on small details to deceive users. By verifying URLs, using trusted resources, and leveraging anti-phishing tools, you can drastically reduce your chances of falling victim to these attacks.
4. Fake Airdrops
What Are Fake Airdrops?
Fake airdrops are one of the most common scams in the crypto space, frequently seen on social media platforms like Twitter (X), Telegram, and Discord, as well as in scam emails. These schemes promise free tokens or rewards to lure victims into compromising their funds or private information.
These scams often come in two main forms:
Fake accounts impersonating legitimate projects, like the example of the HyperLiquid airdrop scam, where victims are directed to a fake website to connect their wallets.
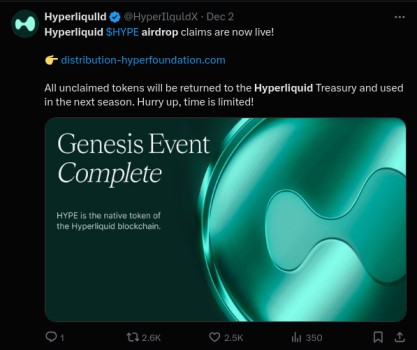
Misleading emails or messages claiming you need to “claim” an airdrop when, in reality, legitimate tokens were already distributed to verified accounts.
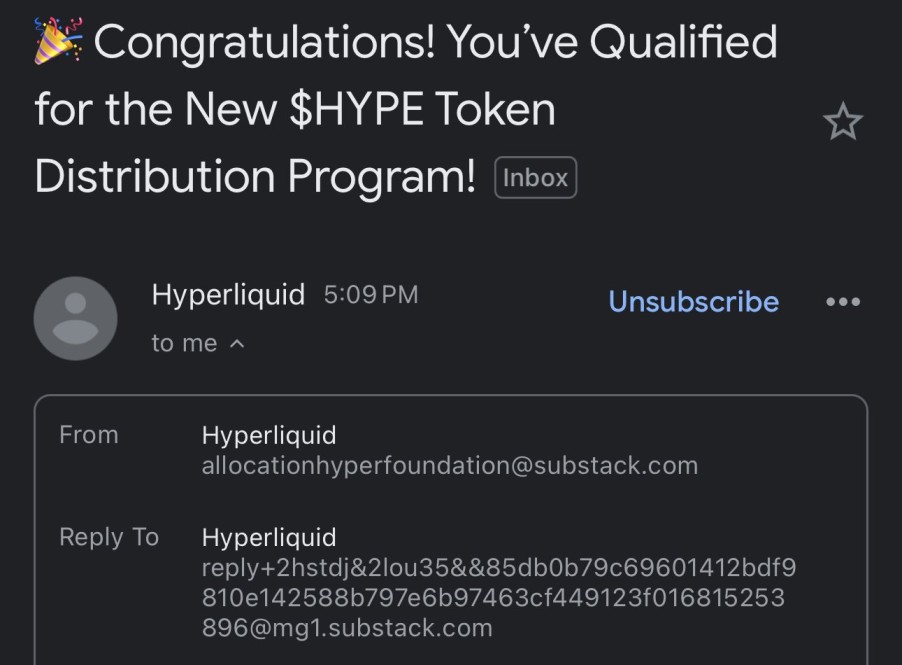
How Do They Work?
1. Fake Wallet Connection Requests:
Victims are directed to a fake website or app that asks them to connect their wallet to claim the airdrop.
Once connected, malicious smart contracts are authorized, enabling scammers to drain funds or execute unauthorized transactions.
2. Phishing Forms:
Scammers create fake forms asking for private keys or seed phrases under the guise of verifying eligibility.
3. Suspicious Token Deposits:
Victims receive random tokens in their wallets, prompting a message like “Claim your reward now.” Interacting with these tokens triggers malicious contracts.
4. Social Media Spam:
Searching hashtags like #airdrop on Twitter often reveals a flood of spam posts. These posts almost always link to scams or engagement farms, not legitimate rewards.
How to Stay Safe
1. Avoid “Too Good to Be True” Offers:
Be skeptical of unsolicited messages or posts promising free tokens, especially those with high-value claims.
Real airdrops rarely require immediate action like wallet connections or payments.
2. Verify Airdrop Announcements on Official Channels:
Cross-check any airdrop information with official project websites or social media accounts.
Use trusted sources like CoinGecko, CoinMarketCap, or project-specific Discord groups for reliable information.
3. Understand the Airdrop Process:
Legitimate airdrops often have clear, pre-announced criteria, such as participation in a points program or wallet activity over months.
For instance, HyperLiquid’s real airdrop was tied to a points system, and tokens were distributed automatically without any wallet interaction needed.
4. Don’t Rely on Social Media Searches:
Avoid searching for “airdrop” hashtags or clicking on random posts. Most of these are scams or engagement bait.
5. Do Your Research:
Legitimate airdrops are usually farmed intentionally by users who study projects, understand their likelihood of distributing tokens, and plan accordingly.
Key Takeaway
If an airdrop seems too good to be true, it probably is. Legitimate airdrops are tied to deliberate user participation, research, and verified platforms. Always stay cautious and never connect your wallet, and remember that private keys should never be shared under any circumstances.
5. Rug Pulls
What Are Rug Pulls?
Rug pulls are one of the most notorious and damaging scams in the crypto space, where developers lure in investors with a promising project only to abandon it and drain liquidity, leaving investors with worthless tokens. The name “rug pull” aptly describes the act of pulling the rug out from under unsuspecting investors.
These scams are particularly common in the meme coin market, where hype and FOMO (fear of missing out) drive new entrants to chase quick profits. Meme coin creators often program malicious smart contract features that allow them to drain funds or prevent token holders from selling.
How Do Rug Pulls Work?
1. Create Hype:
Scammers use social media platforms, influencers, and flashy marketing to promote their project. They often promise high returns or groundbreaking features.
Meme coins frequently employ catchy names, cute branding, or trendy visuals to attract attention.
2. Attract Investments:
Investors flock to buy tokens, often without fully understanding the tokenomics, ownership structure, or risks involved.
Early price pumps create an illusion of success, luring in more buyers.
3. Execute the Rug Pull:
Developers either drain the liquidity pool, dump their large token holdings, or implement restrictions in the smart contract that prevent users from selling their tokens.
The chart below shows the infamous Hawk Tuah token, a meme coin that attracted significant volume before the developer drained funds, leaving investors with a worthless token.
Key Examples of Rug Pulls
Meme Coin Scams:
The Hawk Tuah token gained traction with promises of massive gains, only for the creator to rug the community, wiping out millions of dollars in liquidity.
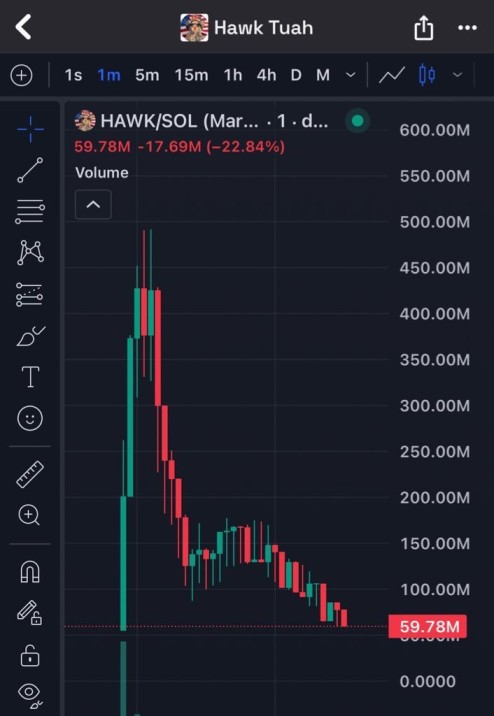
How to Avoid Rug Pulls
1. Avoid Chasing Hype:
Steer clear of projects with massive social media buzz but no clear fundamentals. Real value in crypto comes from building sustainable ecosystems—not pump-and-dump schemes.
2. Research Tokenomics and Ownership:
Analyze the token distribution. If a significant portion of the supply is owned by the team or private investors, this is a red flag.
Avoid projects with anonymous developers or unclear governance structures.
3. Use Rug Pull Detection Tools:
Platforms like De.Fi, Token Sniffer, and SolidityScan can help identify malicious features in smart contracts.
DexScreener and GeckoTerminal integrate contract risk analyses directly into their platforms.
4. Check for Security Audits:
Look for projects that have undergone audits by reputable firms like CertiK or RugDoc. While audits are not foolproof, they add an extra layer of scrutiny.
Key Takeaway
Rug pulls thrive on investor greed and lack of due diligence. Avoid projects that rely on hype and FOMO, and always use available tools to evaluate a project’s risks before investing. If something looks too good to be true, it likely is.
Part 2: More Complex Scams
While the previous scams can be avoided with basic security practices, the following threats require a deeper understanding of DeFi mechanics and more sophisticated prevention strategies. These scams often target experienced users and can be harder to detect at first glance. Stay vigilant and learn how these complex attacks work to better protect your assets.
6. Malicious Browser Extensions
What Are Malicious Browser Extensions?
Malicious browser extensions are fraudulent tools designed to mimic legitimate wallet utilities or offer seemingly useful features while secretly stealing your crypto assets or manipulating your transactions. These extensions appear harmless but are specifically programmed to compromise your wallet security.
Examples include:
An extension claiming to enhance your wallet experience but secretly capturing your private keys.
A “portfolio tracker” or “transaction optimizer” that modifies transaction data to transfer assets to a scammer’s wallet.
Real-World Example: The “Bull Checker” Extension
Recently, the Bull Checker extension targeted users trading on Solana dApps like Raydium and Jupiter. Marketed as a tool to view holders of memecoins, it secretly added malicious instructions to user transactions.
1. How It Worked:
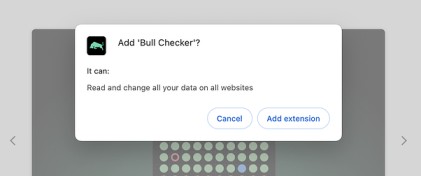
Users installed the Bull Checker extension, which claimed to provide read-only analytics but requested extensive permissions.
When users interacted with legitimate dApps, the extension modified transactions to transfer funds to the attacker’s wallet while displaying a “normal” simulation.
This malicious activity drained multiple users’ funds before it was discovered.
2. Analysis:
The extension was publicized by an anonymous Reddit account targeting memecoin traders.
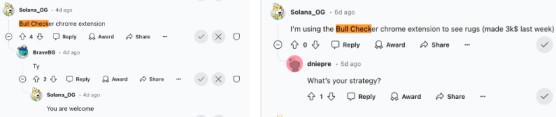
The attack was sophisticated enough to bypass basic wallet simulations.
Example Transactions:
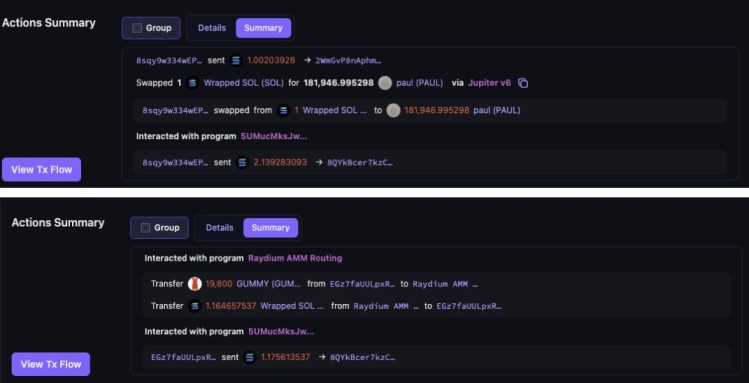
How to Stay Safe from Malicious Extensions
1. Install Extensions Only from Verified Sources:
Download tools directly from official websites or trusted repositories like GitHub.
Always verify the developer and read reviews before installing.
2. Audit Permissions Regularly:
Avoid extensions that request extensive permissions, such as the ability to “read and modify all website data.”
Regularly review your installed extensions and remove those you no longer use or trust.
3. Be Wary of Recommendations:
Don’t trust an extension solely because it’s highly upvoted or mentioned on social media. Scammers frequently use astroturfing and fake reviews to build credibility.
Conclusion
The Bull Checker case is a stark reminder of how sophisticated these attacks have become. Stay vigilant, review every extension you use, and rely only on tools you can verify. Scams thrive on carelessness—don’t give them the opportunity.
7. Dusting Attacks
What Are Dusting Attacks?
Dusting attacks are a relatively new and deceptive type of scam targeting DeFi users across all major chains, including Ethereum, Layer 2s, Solana, Ton, and others. In these attacks, scammers send tiny amounts of tokens—commonly referred to as “dust”—to unsuspecting wallets. While the amounts are small and appear harmless, their purpose is often malicious: to deanonymize wallet owners or trick them into making critical errors.
How Do Dusting Attacks Work?
1. Address Impersonation with Dust Tokens:
Scammers create dust transactions using addresses designed to look similar to ones you’ve previously interacted with.
For example, if you sent tokens to 0xdb99...fed8, a scammer might send you tokens from a fake address like 0xdb99...fed8 (with the same start and end characters).
If you rely on transaction history and only check the first few and last few characters of the address, you could unknowingly send funds to the scammer’s address instead.
Below, a transaction history highlights how addresses and small amounts of tokens could be used to confuse users.
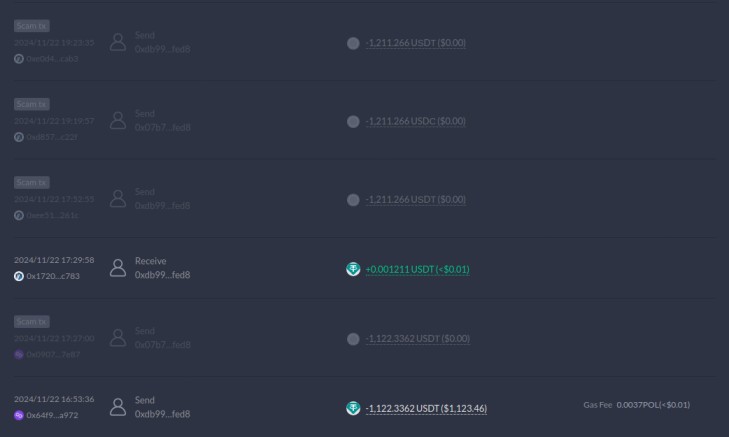
2. Random Token Distribution:
Scammers distribute random tokens or NFTs to multiple wallets. These tokens often mimic legitimate assets but are programmed with malicious smart contracts.
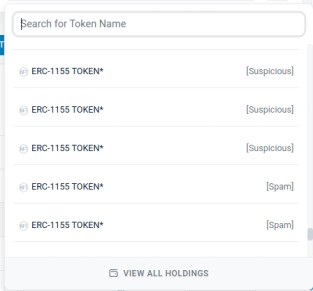
If you interact with these tokens (e.g., approving, trading, or signing), you could unknowingly authorize a transaction that drains your wallet.
3. Deanonymization:
Scammers track how the dusted tokens are used in future transactions, analyzing patterns to link wallet addresses to real-world identities.
This is particularly concerning for individuals managing large balances or running high-value operations.
How to Avoid Dusting Attacks
1. Avoid Interacting with Unknown Tokens:
If you notice unfamiliar tokens or NFTs in your wallet, do not approve, sell, or transfer them.
Consider hiding these assets in your wallet interface to prevent accidental interaction.
2. Verify Wallet Addresses Thoroughly:
Always double-check entire wallet addresses before making a transaction. Tools like Rabby Wallet can help identify and flag suspicious addresses.
3. Use Wallets with Scam Detection:
Wallets like Rabby and platforms like DeBank are designed to identify scam tokens and flag suspicious activity.
These tools reduce the risk of interacting with malicious tokens.
4. Leverage Privacy Features:
Use privacy-focused tools such as Railgun or Fluidkey to obscure your wallet activity. This makes it harder for scammers to track your transaction patterns and target you.
5. Be Vigilant When Copying Addresses:
Scammers rely on users making quick assumptions based on partial address matches. Always copy addresses directly from verified sources.
Key Takeaway
Dusting attacks exploit carelessness and trust. By maintaining caution, using reliable tools, and verifying every transaction, you can protect your assets from these subtle yet damaging scams.
Understanding Evolving Scams in DeFi
The world of DeFi is both innovative and volatile, offering financial freedom and decentralized control—but also attracting an ever-growing number of scams. DeFi has hundreds of different scam types, ranging from classic phishing attacks to highly sophisticated social engineering schemes. What makes these scams particularly dangerous is their constant evolution. As security measures improve, so do the tactics employed by scammers.
One thing is clear: the majority of scams today revolve around tricking users into signing away their funds, often without them even realizing it. Whether it’s through malicious token approvals, fake permit requests, or phishing links masquerading as trusted platforms, the end goal is always the same—steal your assets.
How Scams Target DeFi Users
At the core of most scams is the act of convincing users to interact with malicious smart contracts or sign deceptive transactions. These phishing attempts exploit user trust, confusion, and the complexity of DeFi tools. Examples include:
- Fake Tokens and Approvals: Scammers deploy tokens that mimic legitimate assets. Users unknowingly approve these tokens, giving scammers access to wallets.
- Phishing Permit Transactions: Fake websites or apps ask users to sign “approvals” or “updates,” which secretly grant unrestricted access to tokens.
- Compromised Platforms: Some scammers hack the frontends of legitimate protocols, redirecting users to phishing sites without their knowledge.
Breaking Down Common Tactics
Let’s explore the different ways scammers operate and what users can do to stay safe. Here’s an overview of common scam strategies and victim acquisition methods:
| Category | How It Works | Examples of Phishing Tactics |
| Token Scams | Users are lured into approving malicious transactions that give scammers access to tokens. | – Fake token approvals- Uniswap-style permit requests- Infinite token allowances. |
| NFT Scams | Users approve transfers or interact with malicious NFT contracts, leading to stolen assets. | – “Claim this NFT” scams- Bulk approval transfers- Fake Seaport or X2Y2 listings. |
| Native Token Scams | Scammers use false claims of “security updates” or “reward claims” to gain control of wallet funds. | – Network “mergers” requiring approval- Malicious reward distribution systems. |
| General Scams | Fake signing requests exploit eth_sign and similar features to execute malicious transactions. | – Blanket approvals for smart contracts- Generic transaction signing with vague descriptions. |
Victim Acquisition Tactics
Scammers use multiple channels to acquire victims, making it crucial for users to stay vigilant:
| Platform | How It Happens | How to Avoid It |
| Hacked influencer accounts or fake profiles promote phishing links and fake giveaways. | Verify all announcements on official project websites or trusted channels. | |
| Discord | Fake server invites or malicious bots redirect users to phishing platforms. | Only join verified servers using links from official sources. |
| Airdrop Phishing | Scammers promise free tokens or NFTs but require malicious wallet interactions. | Be cautious of unsolicited airdrop claims, especially from unfamiliar accounts. |
| Scam Ads | Fraudulent Google/Twitter ads redirect to fake platforms designed to steal wallet credentials or funds. | Avoid clicking on ads and always type URLs directly into your browser. |
| Compromised Frontends | Attackers manipulate DNS or supply chains of legitimate sites to serve phishing pages. | Use tools like MetaMask or Rabby Wallet that detect and warn about phishing pages. |
The Bigger Picture
As DeFi grows, so does the sophistication of these scams. It’s no longer just about protecting your private keys but about understanding the mechanics of smart contracts, transaction approvals, and how to spot phishing attempts.
The key takeaway is that almost all DeFi scams today aim to exploit user interactions. Whether it’s signing a malicious transaction, approving a fake token, or falling for a phishing link, the result is often the same—loss of funds.
Part 3: Advanced Solutions to Stay Safe
Before diving into our recommended security setup, it's crucial to understand that no single solution can guarantee 100% security. The key is to implement multiple layers of protection while maintaining a balance between security and usability. The tools and strategies we'll discuss are designed to work together, creating a robust defense against various attack vectors while keeping your DeFi interactions smooth and efficient.
The Trio Setup: Your Core Security Framework
Achieving true security in DeFi goes beyond avoiding scams—it involves adopting tools and workflows that minimize risks while maximizing productivity. Here, we present the ultimate trio for secure web3 interactions: GridPlus, Rabby Wallet, and ENS Subdomains. Together, these tools provide an unparalleled combination of security, usability, and organization for your crypto assets.
1. GridPlus: Setting a New Standard for Hardware Wallets
GridPlus takes hardware wallet security to the next level, combining smartcard-based security with an intuitive, large touchscreen that ensures you know exactly what you’re signing. While traditional hardware wallets like Ledger and Trezor are reliable and widely used, GridPlus offers a superior experience for users seeking maximum security and workflow efficiency.
Why GridPlus Stands Out
- Smartcards for Seed Management:
- GridPlus uses smartcards to store your seed phrase securely. These cards act as physical keys, making it impossible for attackers to extract your private key without both the card and its PIN. You can store multiple smartcards in different locations, reducing risks associated with traditional seed phrase backups.
- Physical Asset Separation:
- Allocate specific smartcards for different wallets or collections. For example, one card can manage your DeFi assets while another handles NFTs. Switching between wallets is as easy as swapping cards.
- Large Touchscreen for Full Transaction Visibility:
- Unlike traditional hardware wallets, GridPlus displays every detail of the transaction directly on its large touchscreen. This ensures you see exactly what you’re signing, which can prevent phishing attempts or malicious transactions that manipulate wallet prompts.
Ledger and Trezor Alternatives
While Ledger and Trezor are excellent entry-level hardware wallets and suitable for most users, GridPlus raises the bar by combining ease of use, unparalleled transaction visibility, and next-level security through smartcards.
2. Rabby Wallet: The Wallet You Always Wanted
Rabby Wallet redefines what a web3 wallet can do, offering features and security enhancements that MetaMask lacks. Designed for seamless multichain interactions, Rabby doesn’t just help you manage your assets—it actively protects them.
Top Features of Rabby Wallet
- Address Whitelisting:
- Rabby allows you to create a whitelist of approved addresses, ensuring you never accidentally send funds to the wrong wallet. This feature is invaluable for preventing costly mistakes.
- Transaction Simulation:
- Before you sign a transaction, Rabby simulates it and shows you exactly what will happen, including any potential risks or unauthorized fund transfers. This protects you from signing malicious transactions, even if you’re interacting with unfamiliar platforms.
- Multichain Support and User-Friendly Design:
- Rabby supports multiple blockchain networks, providing a clean and intuitive interface that streamlines asset management across chains.
Why Rabby Over MetaMask?
Rabby was designed to address the shortcomings of MetaMask. With its focus on security, usability, and advanced features like transaction simulation and address whitelisting, Rabby is the web3 wallet users always hoped for.
3. ENS Subdomains: Security, Organization, and Branding
![Promotional banner for ENS with the text "Welcome to the [New Internet]: A Safer Space Away from DeFi Scams" featuring domain names like "uni.eth," "nba.eth," "ens.eth," and "vitalik.eth.](https://defishills.com/wp-content/uploads/2024/12/ens-1024x363.jpg)
Ethereum Name Service (ENS) allows users to create human-readable wallet addresses (e.g., yourname.eth), but its subdomain functionality takes security and usability to the next level. With subdomains, you can compartmentalize your assets, improve organization, and even build a recognizable brand.
Why ENS Subdomains Are Game-Changing
- Improved Security Through Compartmentalization:
- Assign each subdomain (e.g.,
nfts.yourname.eth,defi.yourname.eth) to a separate wallet address. This ensures that even if one wallet is compromised, the rest remain untouched. For maximum security, each subdomain should be tied to a unique ERC-20 wallet address.
- Assign each subdomain (e.g.,
- Better Organization of Assets:
- Subdomains make it easy to separate and manage your assets. For example, you can dedicate one wallet for NFTs, another for DeFi investments, and a third for airdrops.
- Enhanced Brandability:
- Subdomains allow you to maintain a unified identity across web3 platforms. For instance, if
yourname.ethis known in the community, subdomains likenfts.yourname.ethretain that recognition while adding an extra layer of security.
- Subdomains allow you to maintain a unified identity across web3 platforms. For instance, if
Example Workflow
Imagine using ENS subdomains for compartmentalization:
nfts.yourname.ethlinks to a wallet specifically for NFT collections.defi.yourname.ethis tied to a wallet for farming and liquidity pools.- Both wallets are secured with GridPlus smartcards and managed seamlessly via Rabby Wallet.
The Ultimate Trio Workflow
Here’s how you can combine GridPlus, Rabby Wallet, and ENS Subdomains to supercharge your security and productivity:
- Use GridPlus smartcards to physically separate wallets for different purposes, ensuring no single point of failure.
- Manage transactions safely with Rabby Wallet, utilizing features like address whitelisting and transaction simulation to avoid phishing attacks or costly mistakes.
- Organize and protect your assets with ENS Subdomains, creating a branded and secure identity across wallets.
This combination of tools offers not just security but a fully optimized workflow for interacting with DeFi and web3. Whether you’re managing NFTs, trading on decentralized exchanges, or farming rewards, this setup ensures you can do so confidently and efficiently.
Beyond the Trio: Additional Security Enhancements
Security in DeFi requires constant adaptation and vigilance. The following tools and practices serve as additional layers to strengthen your core security framework, helping you stay protected in this dynamic ecosystem.
4. Revoking Approvals: A Critical Step for DeFi Security
If you’ve interacted with DeFi protocols, you’ve likely granted numerous token approvals to smart contracts. These approvals remain active indefinitely, giving the approved contract permission to access your tokens. While convenient for recurring transactions, leaving these approvals unchecked can pose significant risks. If a smart contract is exploited or compromised, attackers can misuse the granted approval to drain your funds.
Why You Should Revoke Approvals
- Prevent Exploits:
- If a smart contract you’ve interacted with is hacked, your previously approved tokens could be at risk. Revoking approvals prevents this.
- Enhanced Security:
- By limiting token access to only active and trusted protocols, you minimize the potential for malicious exploits.
- Routine Maintenance:
- Over time, wallets accumulate approvals for protocols you no longer use. Cleaning up these unused approvals ensures better long-term security.
How to Revoke Approvals
Revoking approvals is simple and can be done using multiple tools or wallets:
1. Use Dedicated Platforms:
These platforms scan your wallet for active approvals and allow you to revoke them with just a few clicks.
If you use Rabby Wallet, it has a built-in token approval management feature. Navigate to the approvals section in the wallet to view and revoke permissions directly.
2. Best Practices:
- Wait for Low Gas Fees: Revoking approvals involves on-chain transactions, so timing it when gas fees are low can save you money.
- Regularly Check and Revoke: Make it a habit to review and revoke unnecessary approvals every few months or after heavy DeFi activity.
- Focus on High-Risk Approvals: Start with approvals that give access to large token amounts or involve unknown protocols.
Example Platforms for Revoking Approvals
Revoke.cash Interface: Provides a clean overview of all active approvals, including token amounts and associated protocols.
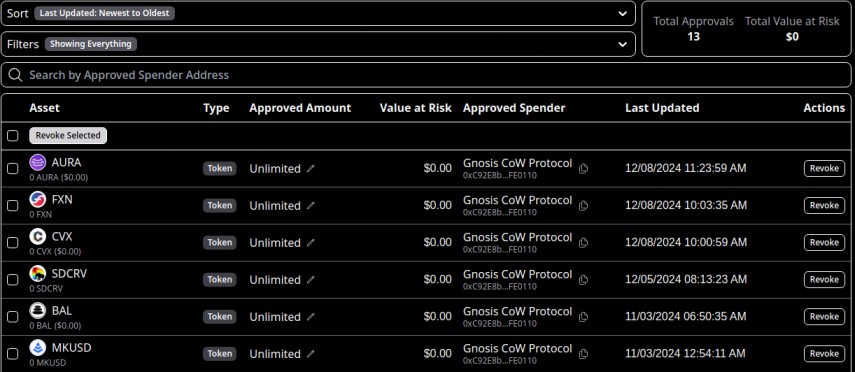
Rabby Wallet Integration: Allows quick revocation of approvals directly within the wallet for a seamless experience.
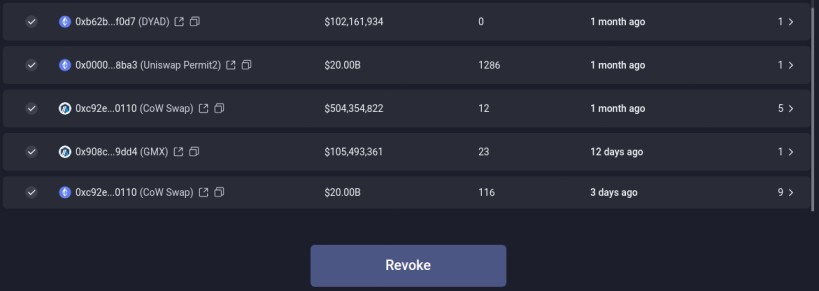
Revoking approvals is a simple yet powerful step in securing your DeFi assets. By proactively managing your wallet permissions, you reduce risks and ensure a safer experience while navigating the evolving landscape of decentralized finance. Make it a regular part of your DeFi security routine.
5. Privacy Tools: Shielding Your DeFi Footprint
As highlighted in the dusting attacks section, scammers and hackers often monitor your on-chain activity to target you with scams, dusting attacks, or other malicious tactics. Protecting your privacy and shielding your transactions can make you a much harder target, while also ensuring your activities remain private from curious eyes.
This is where transaction obfuscation comes into play. By using advanced privacy tools such as Fluidkey and Railgun, you can significantly enhance your on-chain privacy while maintaining control over your assets. Let’s explore how these tools work and why they’re essential for securing your DeFi experience.
Fluidkey: Stealth Addresses for Everyday Privacy
Fluidkey is a practical tool for maintaining privacy in your everyday crypto interactions. It allows you to generate custom ENS addresses that can be shared without exposing your main wallet holdings. Each time you share an address, Fluidkey generates a new stealth address linked to your ENS name, shielding your primary funds and ensuring your transactions are not easily traceable.
Why Use Fluidkey?
Fluidkey is ideal for situations where you need to share an address but don’t want others to see your true balances or wallet activity. For example:
- Personal Payments: If you’re playing online games with friends and need to send or receive winnings in USDC, you can share an address without revealing your total crypto holdings.
- Business Transactions: Use Fluidkey to provide clients or customers with a unique address for payments while keeping your main wallet details hidden.
How Fluidkey Works:
Fluidkey acts as a privacy layer for your ENS address. It disconnects your primary wallet from the shared address while ensuring smooth transactions. Although the generated addresses are public on-chain, they are disconnected from your primary funds, making it significantly harder for scammers to track your financial activity.
Fluidkey seamlessly integrates with the trio framework (GridPlus, Rabby Wallet, ENS Subdomains), providing an excellent privacy-enhancing addition for everyday DeFi users.
Railgun: Zero-Knowledge Privacy for Advanced Obfuscation
If Fluidkey addresses everyday privacy needs, Railgun takes privacy to the next level. Railgun is the leading privacy-shielding tool in the EVM ecosystem, designed to fully obfuscate transactions between two addresses. By leveraging Zero-Knowledge (ZK) cryptography, Railgun enables private use of smart contracts and DeFi protocols.
Why Use Railgun?
Railgun shields your transactions and holdings completely, making them invisible to anyone monitoring blockchain activity. Whether you’re moving large sums of assets or engaging with private DeFi protocols, Railgun provides unparalleled privacy.
Key Features of Railgun:
- Privacy Across Networks: Railgun supports Ethereum, Binance Smart Chain, Polygon, and Arbitrum.
- Full Transaction Obfuscation: Shield transactions so that they’re completely invisible to on-chain viewers, providing protection far beyond simple address disconnection.
- DeFi Compatibility: Use Railgun to interact privately with decentralized exchanges, lending protocols, and other DeFi platforms.
A Trusted Tool: Even Ethereum co-founder Vitalik Buterin has publicly mentioned the value of using privacy tools like Railgun. Its robust privacy framework makes it a vital addition to any security-conscious DeFi user’s toolkit.
Combining Fluidkey and Railgun for Maximum Privacy
Fluidkey and Railgun complement each other beautifully. Fluidkey offers privacy for everyday sharing, while Railgun ensures full shielding for advanced transactions. By combining these tools, you can:
- Prevent scammers and hackers from tracking your activity.
- Shield both casual and high-value transactions from prying eyes.
- Protect your on-chain identity while maintaining seamless DeFi interactions.
Incorporating these privacy tools alongside the trio framework discussed earlier (GridPlus, Rabby Wallet, ENS Subdomains) creates a comprehensive security setup, making it significantly harder for malicious actors to exploit or track your activities. Whether you’re a casual DeFi user or an advanced trader, Fluidkey and Railgun provide the layers of privacy and control needed in today’s evolving crypto landscape.
6. Multi-Signature Wallets: The Ultimate Vault for Your Assets
Multi-signature wallets, or “multi-sigs,” represent the gold standard for securing your most valuable crypto holdings. By requiring multiple approvals for any transaction, they eliminate single points of failure and provide an unparalleled level of protection. These wallets are essential for safeguarding high-value assets, whether you're managing personal reserves, NFTs, or organizational funds.
What Are Multi-Signature Wallets?
Multi-signature wallets require a pre-defined number of approvals (signatures) from designated parties to authorize a transaction. This ensures that no single party or compromised device can execute a transaction without the consensus of others.
How Do They Work?
Multi-signature wallets enforce a collaborative or distributed approach to transaction approvals:
- Pre-Defined Rules: The creator of the wallet sets the required number of signatories for approvals (e.g., 2 of 3 or 3 of 5).
- Shared Access: Each signatory holds their own private key and must sign transactions to meet the approval threshold.
- Enhanced Security: Without the necessary number of signatures, transactions cannot be authorized, protecting funds from unauthorized access.
Personal Use Cases:
With hardware wallets like GridPlus, you can build a multi-sig setup using multiple smartcards as independent keys. For maximum security, store these smartcards in separate locations, ensuring that a single breach cannot compromise your assets.
Best Practices for Multi-Signature Wallets
1. Use Wallets Like Gnosis Safe for Team or DAO Funds:
Gnosis Safe is the industry leader for multi-signature wallets. It supports customizable approval thresholds and integrates seamlessly with DeFi protocols.
Ideal for collaborative projects, DAOs, or organizations with multiple stakeholders.
2. Combine Multi-Sigs with Hardware Wallets:
For personal security, pair your multi-sig wallet with hardware wallets like Ledger, Trezor, or GridPlus.
You can use multiple GridPlus smartcards as independent keys for a robust multi-sig setup.
3. Separate Routine Use from Long-Term Storage:
Use the Rabby Wallet and ENS subdomains for daily operations, while keeping large reserves in a multi-sig wallet.
Only interact with your multi-sig when depositing or withdrawing funds to minimize exposure to phishing attacks.
For a complete guide on how to set up your own smart account (multisig), check out our comprehensive guide on maximizing security with Safe smart accounts.
Why Multi-Sigs Are the Apex of DeFi Security
Whether you’re an individual securing your digital wealth or an organization managing funds, a multi-sig wallet offers peace of mind. When combined with tools like GridPlus, Rabby Wallet, and ENS subdomains, it creates a security framework that is almost impossible to breach. By distributing control and requiring multiple approvals, multi-sigs eliminate the risks associated with single points of failure, making them an essential tool for serious crypto users.
Conclusion
Navigating the decentralized finance (DeFi) space offers unparalleled opportunities, but it also comes with significant risks. Scammers and bad actors evolve their tactics constantly, targeting unsuspecting users through phishing scams, malicious extensions, fake airdrops, and more. Staying ahead of these threats requires more than awareness—it demands action.
Throughout this guide, we’ve covered the full spectrum of DeFi security, starting with the basics and progressing to advanced solutions:
- Identifying and Avoiding Scams: From phishing emails to malicious browser extensions, understanding these schemes is the first line of defense.
- Advanced Security Solutions: The “Trio Setup” of GridPlus, Rabby Wallet, and ENS Subdomains forms a robust security foundation for everyday DeFi users.
- Additional Enhancements: Tools like multi-signature wallets, regular revocation of approvals, and privacy-focused solutions like FluidKey and Railgun offer added layers of protection.
The Future of DeFi Security
While DeFi offers freedom and financial sovereignty, this freedom comes with the responsibility of managing your own security. As scams evolve, so must your defenses. By adopting a proactive mindset and utilizing the strategies outlined in this guide, you’ll significantly reduce your risk and ensure your DeFi journey remains secure and profitable.
Are you ready to take charge of your DeFi security? The tools and knowledge are in your hands. Protect your assets, safeguard your future, and embrace the full potential of decentralized finance—securely. Let’s build a safer, smarter DeFi ecosystem together.


